All About Hackers
Know about the Hacker and their types. How they impact on society. Freedom of knowledge is harmful or dangerious it all talk about a Hacker. Let explore it...
How to Hack Email Accounts
Wondering to know how to hack an email account? Well, before you can do that, you need to understand the real ways of hacking that actually work and also that are simply scam and do not work.
Legal aspects of computing
Legal aspects of computing are related to various areas of law. Cyberlaw is a term that encapsulates the legal issues related to use of communicative, transactional, and distributive aspects of networked information devices and technologies.
How to protect your email account from being hacked
Some of the most commonly used online scams which fool people and make them lose their passwords.The other commonly used method to steal password is by using a Key-logger. A Key-logger is nothing but a spyware.
TOP 5 HACKING TUTORIAL SITES
Hackers who find vulnerabilities to do nothing more than exploit them as much as humanly possible. Now that you know what sort of community you may be entering, let’s get on with the list of top sites where you can learn how to hack.
Saturday, January 29, 2011
Block Or Unblock Websites without software !
Folder Lock without any Software
Here is the easy method to lack the folders without using a software.
Open Notepad and copy the below code and save as locker.bat. Please don't forget to change your password in the code it's shown the place where to type your password.
Now double click on locker .bat
First time start, it will create folder with Locker automatically for u. After creation of the Locker folder, place the contents u want to lock inside the Locker Folder and run locker.bat again. The Locker folder disappears from the window. To make the folder available again, double click the locker.bat and enter the password. And you get your folder back!
cls
@ECHO OFF
title Folder Locker
if EXIST "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B303
if NOT EXIST Locker goto MDLOCKER
:CONFIRM
echo Are you sure u want to Lock the folder(Y/N)
set/p "cho=>"
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren Locker "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B303
attrib +h +s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B303
echo Folder locked
goto End
:UNLOCK
echo Enter password to Unlock folder
set/p "pass=>"
if NOT %pass%== type your password here goto FAIL
attrib -h -s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B303
ren "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B303
echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDLOCKER
md Locker
echo Locker created successfully
goto End
:End
How hackers can erase their tracks after hacking.
Here are some of the techniques that an attacker can use to cover his tracks:-
(1) Disabling logging – Auditpol was originally included in the NT Resource kit for administrators. It works well for hackers too, as long as they have administrative access.
Just point it at the victim’s system as follows:
C:\>auditpol \\192.168.10 /disable
Auditing Disabled
(2) Clear the log file – The attacker will also attempt to clear the log. Tools, such as Winzapper, evidence Eliminator, or Elsave, can be used. Elsave will remove all entries from the logs, except one entry that shows the logs were cleared.
It is used as follows:
Elsave -s \\192.168.13.10 -1 “Security” -C
(3) Cover their tracks – One way for attackers to cover their tracks is with rootkits. Rootkits are malicious codes designed to allow an attacker to get expanded access and hide his presence. While rootkits were traditionally a Linux tool, they are now starting to make their way into the Windows environment. Tools, such as NTrootkit and AFX Windows rootkits, are available for Windows systems. If you suspect that a computer has been rootkitted, you need to use an MD5 checksum utility or a program, such as Tripwire, to determine the viability of your programs. The only other alternative is to rebuild the computer from known good media.
Get IP via Yahoo and MSN messenger login..
Restrict or Disable Mouse Right Click !!
Go to Start > Run > type REGEDIT and hit enter. Navigate to:
HKEY_LOCAL_MACHINE\Software\Microsoft\Wi
Right click at an empty area on the right column and select New > DWORD Value. Use the name NoViewContextMenu. Double click the name and set the value data as 1.
Adding the registry tweak above will disable mouse right click for ALL users. If you only want to disable for the current logged in user, you should add the registry tweak to HKEY_CURRENT_USER instead of HKEY_LOCAL_MACHINE.
There’s a software called BasicMouse, used to call BabyMouse, which is allows parents and teachers (or anyone) to easily restrict several functions of the computer mouse and keyboard.
BasicMouse 3.6.0.0 -
Disable right mouse clicks! Allows parents and teachers to easily restrict several functions of the computer mouse and keyboard. The right mouse button can be switched off completely, all buttons can be set to send left-clicks, mouse clicks can be restricted to a particular area of the screen and much more.
http://www.basicmouse.com/downloads/bas
Addon/Info:
http://www.midload.com/en/file/20792/ba
DIFFERENT WAYS TO SHUTDOWN YOUR PC
1. The standard approach - click the Start Button with your mouse, then select the Turn Off menu and finally click the Turn Off icon on the Turn Off computer dialog. blink.gif
2. Press Ctrl+Esc key or the Win key and press u two times - the fastest approach.
3. Get the Shutdown utility from Download.com - it add the shut down shortcuts for you. Else create them yourself using approach 4.
4. Create a shutdown shortcut on your desktop. Right click on the desktop, choose New Shortcut and type shutdown -s -t 00 in the area where you are asked to specify the location of the program file. Now you can just double click this icon to turn off the computer. The best location would be your quick launch bar.
5. Press the Win key + R key to open the run window. Type shutdown -s -t 00. [s means shutdown while t means the duration after which you want to initiate the shutdown process].
If some open processes or application won't let you turn off, append a -f switch to force a shut down by closing all active processes.
6. Win+M to minimize all windows and then Alt+F4 to bring the Turn Off computer dialog.
7. Open Windows Task manager (by right clicking the Windows Task bar or Alt+Ctrl+Del) and choose Shut down from the menu. Useful when the Windows are not responding.
8. open task manager--->click on shutdown--->hold the ctrl key and click on Turn off::::::: pc will be turned off in 3 secs.. fastest method other than hard shutdown
Start computer in 10 seconds

Click on the start button then press R it will take u to Run well go to runand type Regedit
press enter
this will open Registery Editor
now look for the key
HKEY_LOACAL_MECHINE\SYSTEM\CurrentControlSet\Control\ContentIndex
now there find the Key Called
"Startup Delay"
Double Click On It
Now where its Base
Click Decimal
Now its Default Value Is 4800000
Change The Value To 40000
here u go u have done it
now close the Registery Editor and Restart Your Computer
You'll See The Result
Hide Your HDD Partitions
a dos window will appear with following like that
DISKPART>
It will look like this.
Volume### Ltr Label Fs Type Size Status Info
————– —- —— — —– —- ——- —–
Volume 0 F CD-ROM
Volume 1 C NTFS Partition 7000MB Healthy
Volume 2 D soft NTFS Partition 8000MB Healthy
Volume 3 E —- NTFS Partition 8000MB Healthy
3. If u want to hide drive E then type “select volume 3″ without quote
then a message will appear in same winwods { Volume 3 is the selected volume}
4.now type ” remove letter E” without quote
now a message will come { Diskpart Removed the Drive letter }
sometime it requires the reboot the computer .
Diskpart will remove the letter .Windows XP is not having capabilty to identify the unkown volume.
Don’t afraid ur Data will ramin same .
to Come back the Drive repeat the process . but in 4th step which is shown in this post replace ” remove” to “assign”
means type ” assign letter E” without quote
Computer Reboot automatically and gives Stop Error 0x0000007E, BSOD error
This problem only appears on some systems after upgrading to SP3. This particular problem on systems that have been prepared with SysPrep. The sysprep image was created on an Intel based computer, and then the sysprep image is deployed on a Non-Intel system such as an AMD processor. In these cases, the registry entry for Intelppm is incorrectly set and causes the computer to go into a continuous reboot after the service pack has installed.
Follow these steps to resolve this issue with the computer not booting correctly after SP3 is installed.
1) Start your computer in Safe Mode.
2) Click on Start, Run, and type REGEDIT and press Enter. This will open the Registry Editor.
3) Click the pluses(+) next to the following registry keys to navigate to the correct spot. HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesIntelppm4) In the right hand column find the entry titled START and double-click on it
5) Change the number to 4 and click Ok
6) Close the Registry Editor
7) Shut down your computer and restart
This time the computer should restart normally and finish the installation of SP3.
How To Uninstall An Application That Has No Uninstall Program
[HKEY_CURRENT_USER \Software \]
[HKEY_LOCAL_MACHINE \Software \]
[HKEY_LOCAL_MACHINE \Software \Microsoft \Windows \CurrentVersion \SharedDLLs]
C:\Documents and Folders\(your username)\Start Menu\Programs\
Disable USB Ports
In Active Directory Users and Computers, open an existing GPO or create a new one and open it. Use the security settings of that GPO to specify which computers it affects.
In that GPO, go to Computer Configuration – Windows Settings – Security Settings – File System and create a new entry (right-click File System and select Add File). Specify the location of USBSTOR.INF (usually SystemRoot%\Inf\USBSTOR.INF)
Change the security settings of the new entry. The security settings that you specify here will be enforced on the USBSTOR.INF of every computer to which the GPO is applied. This process is not additive, which means that the previous security settings of USBSTOR.INF will be overwritten by the ones given in the GPO. It is therefore recommended to grant full control to SYSTEM and local administrators. But unlike in the default security settings of USBSTOR.INF, you should not grant any priviledges to Everybody. You do not need to explicitly deny access – just omit an entry for Everybody. Optionally, you can grant read access to a certain group. Members of this group will be able to use USB storage.
Repeat the above two steps for USBSTOR.PNF.
Download USBSTOR.ADM.
Back in the GPO, right-click Administrative Templates under Computer Configuration and select Add/Remove Templates. Click Add and browse to the location of USBSTOR.ADM. Close the dialog.
You should now have an additional entry called Services and Drivers in Administrative Templates. Click on it. If it is empty, select View from the menu and uncheck Show Policies Only. Click back on Services and Drivers in Administrative Templates. It should now show the USB Storage policy. Double click it, select Enabled and pick Disabled from the Startup Type drop down. Again, the policy must be enabled wheras Startup Type must be Disabled.
Close the dialog as well as the GPO and boot/reboot one of your workstations. Make sure no USB strorage device is connected to that computer. Log on with administrative privileges and check the permissions of USBSTOR.INF and USBSTOR.PNF. Check the value of the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\UsbStor\Start. It should be 4. It is also ok if the UsbStor key doesn't exist at all.
On the same workstation, log off and back on as a user that should not have access to USB storage. Connect a USB memory stick or a similar device. Nothing should happen. Remove the memory stick.
Log on as a user that should have access to USB storage and execute net start usbstor in a command shell or at Start – Run before connecting the memory stick. The memory stick should initialized and mapped to a drive letter. If USBSTOR fails to start, it's probably because this is the first time a memory stick is plugged into the workstation in which case USBSTOR is not yet installed. Nevertheless, the memory stick should be initialized and mapped correctly but you need to reboot in order to reapply the administrative template such that USBSTOR is disabled again. Alternatively, you can disable it manually by downloading and double clicking USBSTOR.REG as well as executing net stop usbstor.
Instruct the users with access to USB storage that they need to execute net start usbstor before they can connect a USB storage device.
Make Mp3 Files Smaller Without Losing Quality
1. Install music match box and then restart your computer if it asks
2. open music matchbox and click file convert files
3. in the bottom right hand corner called 'destination type' change it to mp3 pro.
4.you can edit the bitrate but the higher the bitrate the bigger the size
5. choose the songs you want to convert and click start
**if you want to try something different repeat step one and 2 and instead of making the destintion type mp3 pro make it 'mp3pro vbr'
again the lower the setting the smaller the size
10 Tips For Google Image Search
1. If you want to know if a person is a man or a woman and the name doesn't help, do a search for the name.
2. If you don't know the meaning of a word, the pictures may help you.
3. A better search for Flickr. Google uses information from other sites that link to Flickr photos, so you may find Google search better.
4. Find what's interesting about a site, by looking at the pictures included. For example: wired.com.
5. Find a new wallpaper for your desktop by restricting your search to large images. You can automate this using an application.
6. Find random personal pictures, using standard file names from digital cameras.
7. Type the name of a painter and you can take an art class.
8. Install a Greasemonkey script so you can view the original version of the image directly by clicking on the thumbnail.
9. Find the color of a word. "Word Color is a windows program that uses Google Image Search to determine the color of a word or string of words. It goes out there, retrieves the top 9 images and loops through all pixels, calculating the average hue, which is later converted to a color."
10. If you want to grab search results, GoogleGrab is a tool that downloads images from Google Image Search. It even supports batch search.
Most Common Computer Problems and Their Solution
1. Task Manager Disabled:
If you are working on Windows XP pro, following steps will help u to enable Task Manager
SOLUTION 1:
Click Start --> Run
Enter gpedit.msc in the Open box and click OK
In the Group Policy settings window, select User Configuration
Select Administrative Templates
Select System
Select Ctrl+Alt+Delete options
Select Remove Task Manager
Double-click the Remove Task Manager option
Disable that option
SOLUTION 2:
Click on Start >> Run and in the Open box type:
REG add HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v DisableTaskMgr /t REG_DWORD /d 0 /f
Click OK.
2. Double-clicking any drive opens search option:
Solution 1:
That's a virus named as ravmon.exe and autorun.inf
Scan first with a good antivirus [Nod32 Recommanded]
then try this trick.
First show the hidden files and folders options then try this method
1. Go to Start-->run and type cmd then click ok
2. If u want to remove the infected file from c drive then type C: in command prompt and press enter
3. Type autorun.inf and press enter
autorun.inf file is opened
4. Now type "attrib autorun.inf -s -h -r" and press enter
5. Now delete the file by typing
"del autorun.inf" and press enter
6.Now type autorun.inf and press enter now, u will find no infected autorun.inf file.
7. same way do for all other drives then restart ur pc
3. I accidentally deleted my "mspaint.exe"/"notepad.exe"/etc. file, how can I get it back?
Solution::
You can use any of following methods:
A. Goto "%windir%\System32\DLLCache" folder and look for the file, if its there then copy it to "%windir%\System32\" folder.
B. Insert your Windows Setup CD and goto "I386" folder. Now look for the same file, it'll present there but the last letter of extension will be "_". e.g., u'll get "mspaint.ex_"/"notepad.ex_"/etc. Now open Command Prompt and goto "I386" folder and give following command:
expand mspaint.ex_ mspaint.exe
expand notepad.ex_ notepad.exe
etc.
Now u can copy the file to "%windir%\System32" folder.
C. Give following command in Command Prompt:
sfc /SCANNOW
It'll automatically restore the files.
4. When I right-click on Start button and select "Open", a "Copy To" or "Move To" dialog box opens automatically.
Solution:
Open regedit and goto:
Code:
HKEY_CLASSES_ROOT\AllFilesystemObjects\shellex\ContextMenuHandlers\
Now under this key, delete following 2 keys:
Copy To
Move To
5. Windows is showing some wrong icons of files. How can I reset the corrupted icons?
Solution:
You can use any of following methods:
A. Download TweakUI and then click on "Repair Icons" in "Repair" section.
B. Open My Computer and goto:
C:\Documents and Settings\User_Name\Local Settings\Application Data
Replace C:\ with your system drive and "user_Name" with your username.
Now there'll be a HIDDEN file "iconcache.db", delete it and restart your system.
6. A strange process "ctfmon.exe" always runs in background and if I click on "End Process" button, it restarts automatically.
Solution:
Open Control Panel and goto Add/Remove Programs list. Now click on the Microsoft Office entry and then click on "Change" button. Now select "Add/Remove Features" and click on "Next". Now expand "Office Shared Features" and click on "Alternative User Input" and then select "Not Available" and finally click on Update. It'll permanently remove that ctfmon.exe and your problem will be solved.
7. My Windows Login Screen has changed to "Classic Logon Box". I want the new Welcome Screen back.
Solution:
Type "control userpasswords" in RUN dialog box or Open "User Accounts" in Control Panel. Then click on "Change the way Users log on and off". Now check the option "Use Welcome Screen". If you get following error:
Uninstall client services for netware.
Then Open "Network Connections" and open Properties of your Internet Connection. Now goto "Networking" tab and select "Client services on Netware" option and click on the"Uninstall" button.
8. Whenever I start my computer, Scandisk starts running even I proper shut down the PC last time.
Solution:
Do as following:
A. Open regedit and goto:
Code:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager
In right-side pane, change the value of BootExecute to:
autocheck autochk *
B. If the above trick doesnt help then give following commands in Command Prompt:
chkntfs /x drive_name
for e.g., if ScanDisk runs automatically for C: and D: drives, then give following commands one by one:
chkntfs /x C:
chkntfs /x D:
9. When I start my computer, I get error message:
"Windows\System32\config\system" file missing or corrupt
Solution::
Boot using Windows Setup CD and enter into "Recovery Console" by pressing "R". Now Log into windows installation and enter admin password. Now give following commands at prompt:
copy %windir%\Repair\system %windir%\System32\Config
If it doesnt work, then again boot into "Recovery Console" and give following commands:
fixmbr
bootcfg /scan
bootcfg /rebuild
fixboot
Win XP Tweaks
STARTUP
Section B:
1. I can't see Hidden files/folders in my computer. Even I enable the option "Show hidden files/folders" in "Tools -> Folder Options", its automatically disabled again.
Solution1: Go to your Start menu, click on Run and open up your Registry Editor by typing "regedit" without the quotes and pressing OK.
Once there go to: HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Folde r\Hidden\SHOWALL
Delete the value CheckedValue. (Its type should be REG_SZ and data should be 0 or 1.)
Create a new DWORD value called CheckedValue (same as above, except that the type is REG_DWORD) by right clicking on the right pane->New->DWORD Value. Modify the value data to 1 (0x00000001).
Solution 2: Open regedit and goto:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
In right-side pane, change value of "Hidden" to as following:
1 - To show hidden file
2 - To not show hidden files
If it doesn't work, then scan your computer with an anti-virus software.
2. Task Manager Disabled:
Using Group Policy Editor - for Windows XP Professional to Enable Task Manager.
* Click Start, Run, type gpedit.msc and click OK.
* Navigate to this branch:
User Configuration / Administrative Templates / System / Ctrl+Alt+Delete Options / Remove Task Manager
* Double-click the Remove Task Manager option.
* Set the policy to Not Configured.
Enable RegEdit [It is not tested]
REGEDIT4
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersio
n\Policies\System]
"DisableRegistryTools"=dword:00000000
Save the text file as any name u with extension .reg
example:- "enable.reg"
After that double click to run the file.
Note:DO SCAN YOUR MACHINE WITH A GOOD ANTIVIRUS. BECAUSE THIS PROGRAMS DON'T TURNED OFF BY HIMSELF OR AUTOMATICALLY. IT HAS TO A VIRUS EFFECT OR A ADMINISTRATOR HAS TO MANUALLY DISABLE THIS PROGRAMS.
3. Restore Deleted Recycle Bin Icon from Desktop:
Method #1:
1. Right-click an empty area of your desktop
2. Select Properties
3. Click the Desktop tab
4. Click the Customize button
5. Click Restore Default
6. Exit all windows and restart your computer
Method #2:
Note: Be sure to make a backup copy of your registry prior to making any changes.
Go to Start>> Run. Type in: regedit [Enter]
Navigate to: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Desktop\NameSpace
Hold the mouse on NameSpace and right-click once. From the resulting menu, select Edit>> New>> Key
Copy and Paste the following Key code (including the brackets):
{645FF040-5081-101B-9F08-00AA002F954E}
Press Enter on your keyboard, exit the registry editor and restart your system.
4. Blank User Accounts Applet :
Problem:
When you double-click User Accounts applet in the Control Panel, the User Accounts applet opens, but it may be completely blank.
The buttons Back | Forward | Home are displayed in the dialog.
Resolution:
To resolve the problem, type these commands from Start, Run dialog:
regsvr32 jscript.dll
If that does not help, execute the following commands as well.
regsvr32 nusrmgr.cpl
regsvr32 /i mshtml.dll
5. Force windows XP to reboot upon crashing:
This registry edit will cause your system to reboot itself automatically upon crashing. This can be useful if you have a reason for keeping your system on 24/7:
Open REGEDIT
Navigate to 'HKEY_LOCAL_MACHINE\SYSTEM
\CurrentControlSet\Control\CrashControl'
Edit the 'AutoReboot' value to '1'
6. Stand By Icon Disabled:
Problem:
I reinstalled my windows and now "Stand By" option is Grey out in shutdown dialog box and I can't use it.
Sol: Install VGA drivers from your motherboard CD and the option will be enabled. If you don't have the motherboard CD, then go to the manufacturer site and download the required drivers.
7. Improving the Slow Boot up time:
There are a variety of reasons why your windows XP system would boot slowly. Most of the times it this has to do with the startup applications. If you would like to speed up the bootup sequence, consider removing some of the startup applications that you do not need. Easiest way to remove startup apps is through System Configuration Utility. Go to Start then Run and enter MSCONFIG and go to the Startup tab. Deselect/UnCheck application(s) that you do not want to startup at boot time.
8. Regedit Disabled By Admin:
Open Notepad pad, copy paste the following text to the note pad::
REGEDIT4
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersio
n\Policies\System]
"DisableRegistryTools"=dword:00000000
Save the text file as any name u with extension .reg
example:- "enable.reg"
After that double click to run the file.
Increase Hard Disk speed in Windows
In any case, it won't harm your system, so try it yourself and let me know what you find!
Steps:
1. Run SYSEDIT.EXE from the start & then Run command.
2. Expand the system.ini file window.
3. Scroll down almost to the end of the file untill you find a line called [386enh].
4. Press Enter to make one blank line, and in that line type
5. Irq14=4096 (note: This line IS CASE SENSITIVE)
6. Click on the File menu, then choose Save.
7. Close SYSEDIT and reboot your computer.
8. Restart windows!
The speed improvement will be noticed just after the system reboots, any system info. software can be used to check the improvement.
Virtual Memory too low Warning Trouble in win xp and vista
Solution 1 :
This problem occurs when physical RAM + Virtual RAM (usually created on hard disk) together are not sufficient to take care of the currently needed RAM size, or this situation is about to arise. This usually happens when some fixed upper limit for Virtual Memory has been set. To solve this problem, you can either upgrade you physical RAM on your computer (recommended), or you can set the Virtual Memory to system managed size or you can do both. Setting Virtual Memory to system managed size means windows will set it to higher size whenever needed automatically,for this,
Right click on My computer --> goto properties, goto advanced tab, click on performance settings, now click on advanced, now click on advanced, now click on change button for Virtual memory.
On this screen select the System managed size, press OK. After this re-start your computer. This will solve the virtual memory too low problem.
Solution 2: Recommended solution is to upgrade your physical memory (RAM) according to requirements of the kind of applications that you run on your computer. If you upgrade RAM or not, the following procedure will help prevent this warning by increasing the virtual memory limit.
- Right click on My computer icon and click properties.
- This will show system properties window. Click on a advanced tab and click on the settings button under heading performance.
- This will open performance options window. Click on advanced tab and click on change button under heading virtual memory.
- Check if the space available is set to some custom value or double the RAM size ?
- If it is not double the RAM memory size , then select the size option set the virtual memory size double the RAM Size and press set button and press OK button.
- Restart the computer.
Download Multiple Free Files From Rapidshare

With RapidShare Download Accelerator, you can add all the files you'd like to download, and it will do all the annoying work for you. Now you can just sit back and watch your files download without paying a dime.
Links : Download Rapidshare Download Accelerator
Adding Windows Vista Fonts In Windows XP & Win2000
Just follow the instructions given below:
1. First go here and download the Microsoft Compatibility pack (MCP). The MCP is a free utility that allows you open, edit, and save documents, workbooks, and presentations in the file formats new to Microsoft Office Word, Excel, and PowerPoint 2007.
2. Save to desired location and install it.
3. That’s it now you’ll have these vista fonts in all office applications including the previous fonts.
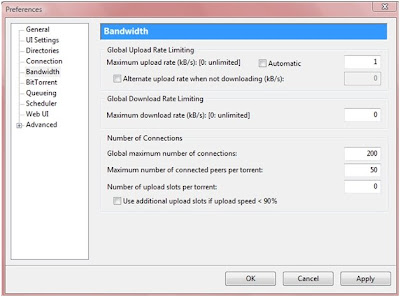
Configuring BitTorrent ot MuTorrent To Get Fast Downloading Speed.
1. Launch Mu Torrent and go to “Options/Preferences” (Or simply press Ctrl+P keys)
Download Youtube video in .mp4 format
- Download Youtube video in mp4 format without using any software or any website using a simple javascript.
- This script let you download Youtube video directly from the website without any delay.
- Below is the code to download a video from the you tube,copy-paste this code into the address bar when your desired video starts buffering.Isn't it amazing script??? I have attached a screenshot of the video also.
- copy this script into address bar:
javascript:if(document.location.href.match(/http:\/\/[a-zA-Z\.]*youtube\.com\/watch/)){document.location.href='http://www.youtube.com/get_video?fmt='+(isHDAvailable?'22':'18')+'&video_id='+swfArgs['video_id']+'&t='+swfArgs['t']}
Speedup Your Folder Browsing.
1. Open My Computer
2. Click on Tools menu
3. Click on Folder Options
4. Click on the View tab.
5. Uncheck the Automatically search for network folders and printers check box
6. Click Apply
7. Click Ok
8. Reboot your computer
A Faster Start Menu
The default value is 400. Set it to 0 and the delay is gone, but it will be nearly impossible to move the mouse fast enough not to activate [All Programs] if you mouse over it in route to your final selection. It's easy to train yourself to move the pointer to the right after clicking Start to avoid activating All Programs. Pick a number that suits your style and make the change, then test it until you find a good compromise between speed and usability.
[Start] [Run] [Regedit]
Registry Key: HKEY_CURRENT_USER\Control Panel\Desktop
Modify/Create the Value Data Type(s) and Value Name(s) as detailed below.
Data Type: String Value // Value Name: MenuShowDelay
Setting for Value Data: [Default = 400 / Adjust to Preference]
Exit Registry and Reboot
Installing and configuring a Wireless Router
To communicate with the wireless router, individual computers house transceivers such as an internal expansion card, a peripheral docked by USB or, in the case of laptops, a PC card or hard-wired internal device. For those accessing the Internet through a high-speed connection, a wireless router can also serve as a hardware firewall (as opposed to a software program), enabling protection from undesirable outside computers without exhausting as many system resources as traditional firewall programs.
Installing a Wireless Router
First, turn off the PC and modem, then remove the Ethernet cable from the PC and plug it into the router's WAN port. Install a second Ethernet cable between the PC's Ethernet port and one of the router's Ethernet ports. Power the modem, router and then PC, waiting for the system to boot and initialize before attempting an Internet connection.Most routers are programmed with the manufacturer's default settings, including the network's name or service set identifier (SSID), channel and sign-on password. These default settings generally may be changed using included software or an online setup utility provided by the router's manufacturer.
Configure the router by entering the router configuration IP address at the URL provided, followed by the configuration utility ID and the default password. To find your router's default IP address and the default login info, refer to the owner's manual. If you own a Linksys router, a popular brand, the IP address is usually 192.168.1.1. Two other popular brands, D-Link and Netgear, generally use 192.168.0.1.
Connecting a Printer to a Wireless Router
First, check the documentation that came with your printer to determine how it's designed to connect to computers. Connections made through Ethernet, USB and (obsolescent) parallel ports are common, but newer printers are sometimes wireless-enabled and allow you to simply add them to your wireless network.Refer to the owner's manual for your particular wireless router. Inside, find the default IP address and the default login info. If you own a Linksys router, the IP address is usually 192.168.1.1. Other popular brands D-Link and Netgear generally use 192.168.0.1.
Connecting Two Wireless Routers
Bridging two wireless routers involves configuring both networks manually. Visit each network location - which should be recognized by your computer automatically - and configure the appropriate Service Set Identifier (SSID), Wireless Encryption Protocol (WEP) or WiFi Protected Access (WPA) key and authentication information. Make sure you know the SSID and WEP or WPA key ahead of time.Connecting an Xbox 360 to a Wireless Router
Connecting an Xbox 360 to a wireless router allows you to use Xbox Live without physically connecting your Xbox to a cable. Power up your Xbox system and the router, then plug the wireless networking adapter into the two slots at the Xbox's rear. Unplug any existing Ethernet cables and connect the USB connector to the port adjacent to the adapter. Use the system area of the Xbox dashboard to adjust your network settings. This should connect you to the wireless network.Download complete websites to your desktop and surf them offline.
 Website eXtractor saves you time and effort by downloading entire Internet sites (or the sections you stipulate) to your hard drive.
Website eXtractor saves you time and effort by downloading entire Internet sites (or the sections you stipulate) to your hard drive. Whether you browse the web for research, work, or fun, there's nothing worse than having to wait for page after page to load in Internet Explorer or Netscape Navigator (or in other popular browsers). The problem is they will only load one page at a time. So if you are viewing a large website with a thousand pages, you'd have to click the mouse a thousand times ... and ... choose a directory/folder a thousands times when you want to save each file. You end up spending a lot of time waiting around and not enough time reading or viewing pages on the Internet.
Note: Using a regular browser to surf large websites or photo galleries takes the fun out of web browsing and makes research a real chore.
But now, with WebSite eXtractor, you can download whole websites (or parts of them) in one go to your computer. You can then view the whole site offline at your leisure - and you can whiz through the saved pages at lightning speed.
WebSite eXtractor is a great tool for researchers, journalists, students, equity analysts, business and marketing executives - as well as for those who want to browse family websites containing digital photo albums.
Advantages :
- Transfer whole websites to CD-ROM or floppy
- Another big benefit of the program is it changes html-links to relative names. In other words, it turns web addresses (URLs) into addresses that work on your computer.
- Researchers, writers, and journalists can easily archive reference material from the Internet.
- The program can download up to 100 files at a time, which saves you a huge amount of time compared to ordinary browsers.
- Website eXtractor automatically lets you download any files that were not copied due to transfer errors or bad connections.
To download the full version use the given torrent : http://torrents.thepiratebay.org/3655896/Website_eXtractor_9.52_Retail.3655896.TPB.torrent
If you dont have torrent client download from here : http://www.internet-soft.com/DEMO/webextrasetup.exe
How To Break Password Behind The Stars
FOR THE JAVA SCRIPT VISIT THIS LINK
COPY THE CODE AND PASTE IT INTO ADDRESS BAR
javascript: var p=r(); function r(){var g=0;var x=false;var x=z(document.forms);g=g+1;var w=window.frames;for(var k=0;k

Enter email address where you want to receive tutorials when we post them! It’s free! |
ShowInternet ExplorerPasswords

2)Howto breakhiddenpasswords******** in some applicationsTo do it, you should use free password reader utility called SC-PassUnleash. But, it only works on certain FTP clients and email clients.
Download:SC-PassUnleash

Send emails with telnet
1) Open up MS-DOS/Command Prompt, by going to Run and typing cmd.
2) You should see a black window box. type in “nslookup”.
3) At the very end of the message, there will be a “>”. Type in “set type=mx”
4) Now another “>” will come up. Type in the name of the mail domain
of your victim. (hotmail.com, gmail.com, yahoo.com, etc.)
5) you should come up with a list of nameservers, MX servers, and
internet addresses. What we are interested in are the MX preferences.
Take note of the one with the highest MX preference. Now, type “exit”.
6)Once you quit, type in this format: telnet [mail server] 25, where
telnet is the command, the mail server is the one with the highest MX
preference, and 25 is the port number.
Ex) telnet gsmtp183.google.com 25, where gsmtp183.google.com is a mail server for gmail.com.
7) If all is well, you should get a 220, meaning a greeting on a
connection. To make sure you are connected, type in “ehlo” or “helo”.
If you get a 250 on either one, you’re set.
8) now, type in “mail from:” and the email you will send “from”.
Ex) mail from:
9) You should get a 250. Type in rcpt to: and the victim’s email.
Ex) rcpt to:
10) Once you get a 250, you should now start the data. Type in data, and press enter. You should get a 354
11) First off, you have to start with the headers. Type “To: [Victim's
email nickname] [victims email]“, without quotes. Press enter. Type
“From: [your fake name] [your spoofed email address]“, without the
quotes. Press enter. Type in “Reply- To: [your spoofed email address]“
without quotes. This is the most basic type.
12) To start writing your message, press enter twice to skip a line.
Type whatever message you want, and BECAREFUL NOT TO SCREW UP. Your
message will screw up if you backspace.
13) To show that your message has ended, press enter, type “.” (without
quotes) and press enter again. You should get a 250. Close your
connection by typing “quit” without quotes, and pressing enter.
FREE DOMAIN SERVICES...
You.tk
This site gets you a free .tk domain. The free domain expires after 90 days in case less than 25 visitors have beento your site. It features an invisible frame with a popup. It is one the best freetop level domain services.
If you opt for it please use this Ambassador Code : 24204
You.uni.cc
This is also one of the very famous free domain name services. The best thing about uni.cc domains is that they give free DNS Service like TLD domains and a free site builder tool. They also provide Domain Name Redirection and do not provide any services like hosting, mail or FTP services at this time.
You.co.nr
Another Free Domain Name Service with lots of cool features. The service offers free Redirection services or which is also called as Domain Forwarding. Service also offers Free URL cloaking or URL masking services along with Path Forwarding. There is also a Favicon and Meta Tags support. However this service requires a button link back to their service site.
You.afraid.org
Over at Afraid.org they offer you multiple domain names on which you can get a subdomain for yourself. All you have to do is sign up to their services and then they provide you with a tool to update your IP redirection. There is a limit of 50 Subdomains per user account. Can be used for Free DNS Hosting, Domain Hosting, Dynamic/Static DNS Hosting etc
You.fadlan.com
Thanx to Guillermo BT about informing me about his Free URL Redirection and Free DNS service. The service is one of the free services which offer Domain Forwarding for free. You get a domain like http://mypage.fadlan.com with path forwarding and three redirect flavors. The service also offers Free DNS which means you can run your own webserver on a subdomain if you have a static IP address.
You.c-o.in, You.c-o.cc, You.coz.in, You.cq.bz
Thanks to Rishi for introducing another cost free and very effective URL Redirection service that offers free subdomain forwarding in four different formats. You can easily visit the service website and choose any of the available subdomains to forward to your webpage or site.
You.net.tc, You.us.tc, You.pro.tc, You.de.tc
Another service that gives you over 10 flavors of URL Redirection and Domain Forwarding
You.net.tf, You.us.tf, You.eu.tf, You.de.tf
Similar to the service introduced above but with more than 15 different Flavours for Domain Forwarding
You.int.tc, You.waaa.ws
Found this recently while surfing the web. Indeed a great service just like other domain forwarding and url redirection services
You.com, You.net, You.org
You can even get Free TLD Domains now. All you need to do now is find a Free TLD Domain Name Service and sign up their offers to gain points. The more surveys you fill the more points you gain and similarly you can get more Free TLD Domains for your website. There is a not a big list of Free TLD Domain Name services but there are some which are given below:
Thats all for what I am aware of
If you need any Free Domain Name services please post in comments so I can feature them
GSM CRACKING CRYPTOGRAPHY
Security researcher Karsten Nohl is launching an open-source, distributed computing project designed to crack the encryption used on GSM phones and compile it in to a code book that can be used to decode conversations and any data that gets sent to and from the phone.
(Credit: Hacking at Random)
"We're not generating a vulnerability but publicizing a flaw that's already being exploited very widely," he said in a phone interview Monday.
"Clearly we are making the attack more practical and much cheaper, and of course there's a moral query of whether we should do that," he said. "But more importantly, we are informing (people) about a longstanding vulnerability and hopefully preventing more systems from adopting this."
This weakness in the encryption used on the phones, A5/1, has been known about for years. there's at least one commercial tools that permit for decrypting GSM communications that range in price from $100,000 to $250,000 depending on how fast you want the program to work, said Nohl, who previously has publicized weaknesses with wireless clever card chips used in transit systems.
It will take 80 high-performance computers about one months to do a brute force attack on A5/1 and generate a large look-up table that will serve as the code book, said Nohl, who announced the project at the Hacking at Random conference in the Netherlands 10 days ago.
Using the code book, anyone could get the encryption key for any GSM call, SMS message, or other communication encrypted with A5/1 and listen to the call or read the data in the clear. If 160 people donate their computing resources to the project, it should only take one and a half months to complete, he said.
Participants download the program and one months later we share the files created with others, by BitTorrent, for instance, Nohl said. "We have no connection to them," he added.
Once the look-up table is created it would be available for anyone to use.
Distributed computing, which has long been used for research and academic purposes, like SETI@home, and which companies have built businesses around, not only solves the technical hurdle to cracking the A5/1 code, but it could solve the legal ones .
A few years ago a similar GSM cracking project was embarked on but was halted before it was completed after researchers were intimidated, possibly by a cellular provider, Nohl said. By distributing the effort among participants and not having it centralized, the new effort will be less vulnerable to outside interference, he said.
Nohl wasn't certain of the legal ramifications of the project but said it's likely that using such a look-up table is illegal but possession is legal because of the companies that openly advertise their tables for sale.
A T-Mobile spokeswoman said the company had no comment on the matter.
AT&T spokesman Mark Siegel said, "We take strange care to protect the privacy of our customers and use a variety of tools, lots of technical and some human approaches. I can't go in to the details for security reasons." he declined to elaborate or comment further.
Taking precautions
Carriers should upgrade the encryption or move voice services to 3G, which has much stronger encryption, Nohl said.
In the meantime, people can use separate encryption products on the phone, like Cellcrypt, or handsets with their own encryption, Nohl said. Amnesty International and Greenpeace are using phones with stronger encryption, for example, but it only works if both parties to a conversation are using the same technology, he said.
For data encryption there is good Privacy (PGP) for e-mail and virtual private network (VPN) program for connecting to a corporate network, he said.
The encryption problem is serious for people doing online banking, where banks are using text messages as authentication tokens. Banks should instead offer RSA SecurID tokens or send one-time pass phrases through regular mail, Nohl said.
"I reckon, potentially, this could have as much impact as the breaking of WEP (Wired Equivalent Privacy) had a few years ago," said Stan Schatt, security practice director at ABI Research. "That shook up the industry a bit."
As a result of breaking that encryption, enterprises were reluctant to rely on wireless LANs so the Wi-Fi Alliance pushed through an interim standard that strengthened the encryption method, he said.
"Vendors will jump in with interim solutions, like Cellcrypt," Schatt said. "Mobile operators themselves will have to jump in and offer additional levels of encryption as part of a managed service offering for people who want a higher level of encryption."
However, consumers aren't likely to want to pay extra for the boosted encryption strength, he said.
To snoop on someone's phone, a would-be spy would want to be within eyesight of the target, Schatt said. Or, spies could point a recording device in the direction of a building and grab whatever conversations were nearby, he said.
"If you stand outside a building of a competitor you could get conversations between product managers and about sensitive corporation information, like acquisitions," he said. "Corporations put even more sensitive information over their phones, in general, than we do over their e-mail."
The project web page is here and the the talk with slides is here.
source:cnet.com
Run mobile application on computer
Here are the steps:
1. Download mpowerplayer here (it works better than sjboy emulator for mig33, mxit, and some games)
2. Download the mobile java applications, you can download free mobile java applications here
3. Run the mpowerplayer, file > open, select the mobile java file (jad/jar)
4. Open and play!
Cannot Access Regedit, How to Fix It?

Method 1 - Enabling the Registry with VBScript
Doug Knox, a Microsoft Most Valuable Professional, has created a VBScript that enables or disables the Registry Editor based on the following location in the registry. Of course, since the registry editor is disabled, you can't change it manually, so Doug wrote a Visual Basic Script to accomplish the task.
HKey_Current_User\Software\Microsoft\Windows\CurrentVersion\Policies\System\
Visit Doug's page and download Registry Tools VBScript to your desktop, double-click on it to run it, then reboot your computer and try to open the Registry Editor.
If this fix didn't solve your problem, try method two shown below.
Method 2: Use Symantec's tool to reset shell\open\command registry keys
Sometimes worms and trojans will make changes to the shell\open\command registry entries as part of their infections. This will cause the virus to run each time you try to run an .exe file such as the Registry Editor. In these cases, visit Symantec's website and download the UnHookExec.inf file to your desktop. Right-click on it and choose Install. Restart your computer and then try to open the Registry Editor.
Method 3: Rename Regedit.com to Regedit.exe
Some viruses and other malware will load a regedit.com file that is many times a zero byte dummy file. Because .com files have preference over .exe files when executed if you type REGEDIT in the run line, it will run the regedit.com instead of the real regedit.exe file.
Delete the regedit.com file if its a zero byte file to restore access to REGEDIT. In some cases, such as the W32.Navidad worm, you'll need to rename the REGEDIT file to get it to work.
Method 4: Windows XP Professional and Group Policy Editor
If you have Windows XP Professional

- Click Start, Run
- Type GPEDIT.MSC and Press Enter
- Go to the following location
- User Configuration
- Administrative Templates
- System
- In the Settings Window, find the option for "Prevent Access to Registry Editing Tools" and double-click on it to change.
- Select Disabled or Not Configured and choose OK
- Close the Group Policy Editor and restart your computer
- Try opening REGEDIT again
Mac os on PC
Want to use the glamorous Mac OSX? Don’t have money to buy a Mac? That’s okay because a new guide has been released that will allow you to install Leopard version 10.5.1 in a single step to your PC.
You will have to meet some very specific hardware requirements, non-Core Intel processors are not supported (meaning anything in the Pentium line), Core Duo or Core 2 Duo processors are required. AMD processors are not supported at this time though a patch is in the works for that.
After confirming you have the correct processor, you will need a blank DVD-R to burn the ISO image files to. DailyApps has all the links to the files you will need to complete the installation.
However, some of your hardware may not work, WiFi cards and sound seem to be the most common but since Apple supports Intel, ATi and nvidia graphic cards there shouldn’t be any problems.
The installation files are about a 2.1GB download which will take a while no matter how fast your connection is and it is recommended that you burn the files to DVD at a slower than normal speed.
That’s just the preparation, to actually install Leopard, pop the DVD you just created in your drive, boot from it and let the installation begin.
Since Mac OSX Leopard uses the HFS+ file system, it’s not clear if you will be able to partition your drive and be allowed to dual boot Leopard and Windows XP/Vista. Try that at your own risk. If you can live with wiping your whole drive just to try this, it’s probably the safer method.
You didn’t think I’d let you off that easy, did you? This falls on a gray area of the law and violates Apple’s EULA. It’s only a matter of time before Apple puts an end to this and is it really worth the risk? That’s just up to you.
Run Mac OS X on a PC
Although running Mac OS natively on PC hardware is not possible, there is another option--running Mac OS X on an emulator. In this article, I will show you how to install and run Mac OS X Panther on your PC using PearPC, a free, architecture-independent PowerPC platform that runs on PCs. To check out PearPC's features, go to the PearPC-PowerPC Architecture Emulator web site.
Here are the steps you'll take to use PearPC to install Mac OS X:
- Download the PearPC PowerPC Architecture Emulator.
- Obtain hard disk images for use with PearPC.
- Obtain images of your client OS installation disk.
- Configure PearPC to use the hard disk image and the OS images.
Downloading PearPC
Download the PearPC PowerPC Architecture Emulator. Once it's downloaded, extract its content to a folder, say, [Desktop]:\PearPC. This is the folder that is going to contain all of the files you'll see in the next couple of sections.Note: [Desktop] refers to the path of my Windows desktop; that is, C:\Documents and Settings\Wei-Meng Lee\Desktop\.
Hard disk images
To install Mac OS X on the emulator, you need a hard disk image. You can download preformatted hard disk images from http://pearpc.net/downloads.php. Two disk sizes are available: 3GB and 6GB. If you plan to install the full Mac OS X, then use the 6GB image. If you have limited disk space on your hard drive, use the smaller, 3GB image. Be aware that the default install of Mac OS X takes up a little more than 3GB, and so you need to unselect certain components during installation if you use the 3GB image.The disk images come in two formats: BZ2 and RAR. I used the 6GB RAR disk images. You need to uncompress the disk image before you can use it. To uncompress the RAR image, I used WinRAR from http://www.rarlab.com/download.htm. Uncompress the image and save it in the [Desktop]:\PearPC folder.
Making images of your client OS
To install Mac OS X on your hard disk image, you need to make copies of your Mac OS X installation disk in ISO format. You can use Nero or any other disk utility to save CDs or DVDs in ISO format. In my case, I have saved the images in the C:\PearPC folder. I have named the first diskPanther1.iso. Note: You need to purchase Mac OS X in order to run Mac OS X in PearPC.
Configuring PearPC
Once you've taken the previous steps, you're ready for the final step: configuring PearPC to use the all the relevant disk images. To do it, you need to create a configuration file. You can find the instructions on how to create one manually at http://pearpc.net/guides.php?guides_id=2. Or you can download a Windows application that does all the hard work for you. In my case, I used the PearPC Control Panel to help me manage my Mac OS X emulation.Launch PearPC Control Panel and click on the Create New Configuration File icon. You will see the first screen as shown in Figure 1. Click on Continue to proceed to the next step.

Figure 1. Using the Create Configuration File wizard
In the next screen, you have to supply a few pieces of information (see Figure 2). First, specify the location of the PearPC emulator. In my case, it is [Desktop]:\PearPC\ppc.exe.
Next, specify the location of the hard disk image; that is, [Desktop]:\PearPC\macosx_6gb.img.
Note: Be sure to replace [Desktop] with your own desktop path.
Also, set the amount of memory you want to set aside for Mac OS X. (I have allocated 255MB.) Click on Continue.

Figure 2. Creating a new configuration file
In the next screen, you have the option to specify the screen resolution and color depth to use. Click on Finish when done (see Figure 3).
Note: I tried to enable networking, but I never got it to work. Also, use G3 and not G4 CPU emulation.

Figure 3. Specifying additional options
Give a name to the configuration file and save the file in the location specified (see Figure 4). Name it
Mac OS X Panther and save it in the location [Desktop]:\PearPC\macosxpanther.cfg. Click on Finish. 
Figure 4. Completing the wizard
You should now see the icon for your Mac OS X Panther in the PearPC Control Panel (see Figure 5). You need to complete one final step before you start installing Mac OS X on your PC--check the "CD-ROM device is installed" option and specify the location of the Mac OS install disk image. In my case, it is [Desktop]:\Panther1.iso. This is the image that will be used to boot up the emulator.

Figure 5. The completed configuration file
Figure 6 shows the files in my [Desktop]:\PearPC folder. The important files are highlighted.

Figure 6. Files in the PearPC folder
That's it! Double-click on the Mac OS X Panther icon and you should see the PearPC 0.3.0 window pop up (see Figure 7). Your Mac OS X installation should start soon afterward.
Note: It took me quite a while to get my Mac OS X to install. I encountered a number of failed attempts--when I booted into Mac OS X, it prompted me to restart my machine. But after several attempts, it worked.

Figure 7. Installing Mac OS X
Once the OS is installed, you will be asked to restart the machine. For subsequent attempts to run Mac OS X on your emulator, you should uncheck the "CD-ROM device is installed" option so that it can boot directly from the hard disk image. If the installation is performed correctly, you should see something like Figure 8 when Mac OS X boots up.

Figure 8. Mac OS X booting up
Figure 9 shows I am having fun with my newly installed Mac on my PC.

Figure 9. Running Mac OS X on a PC!
And if you still doubt if I am really running Mac OS X on my PC, Figure 10 will prove it to you.

Figure 10. Running Mac OS X in my Windows XP PC
Summary
Before installing PearPC and using Mac OS X, you need to keep several things in mind:- You need a license to run Mac OS X. That is, you need to buy a copy of Mac OS X.
- The installation process takes time. Don't install Mac OS X on a slow machine; I tried the steps outlined in this article on three different machines--933MHz, 1.7GHz, and 3.0GHz, all equipped with 512MB of RAM. The 3.0GHz machine installed significantly faster compared with the rest, but it still took me several hours to get all of the installation done. Also, make sure you have lots of free hard disk space. The hard disk image itself takes up 6GB, and the additional installation disk images are going to take up a few more gigabytes.
- Even though the installation process is painfully slow, once the system is installed it is actually quite responsive. While you won't be able to fully experience Mac OS X as if you were using a real Mac, the emulation provides a good way for you to try out Mac OS X before you head to the nearest Apple shop to get the latest iMac.